Jenny Tan is currently leading a global internal audit practice, including IT audit, with a global real estate cum fund management MNC. Outside of work, Jenny volunteers heavily in the technology community space where she actively promotes technology (including cyber) awareness and adoption to both the business and IT professionals and organisations. She is currently the President of ISACA SG Chapter. She is the winner in 2022 Top Woman in Security (SG & Asean), 2022 Women Program of the Year Award (Asia), 2021 Women in IT Outstanding Contribution Award (Asia) and 2021 SG 100 Women in Tech recipient. She has also received the Top 20 Cybersecurity Women in Singapore, 2020 award.
With the lightning speed of technology and digital development, human-centric risk assurance should take priority in all business aspects. To the contrary of what most management and organisations are thinking that technology &/or post digitalization, risk management can be replaced by automation, I offer different opinion on this matter. Granted that technology and automation can greatly complement risk management effort, they are not full-proof. In this article, I hope to share some of my views to offer some help to organisations when they consider enhancing their risk management. And the best value of adopting or adapting some of my recommendations requires zero external costs.
Despite the hot topics about machines/ technology replacing human effort, everyone should take a deep breath, keep cool and step back to “truly see” the “digital landscape” holistically. Human resources design, develop, implement and use these digital and technological solutions. Hence, there are talks about bias and ethics when rolling out the solutions and there is negligence when using the solutions. The technology itself has nothing to be blamed. So, when one performs risk assessment, regardless of technology applied &/or deployed, human-centric risk-based controls cannot be ignored. By the way, processes are initiated and effected by human resources.
Let us understand the simple human-centric risk assurance components that I’ve conceptualized:
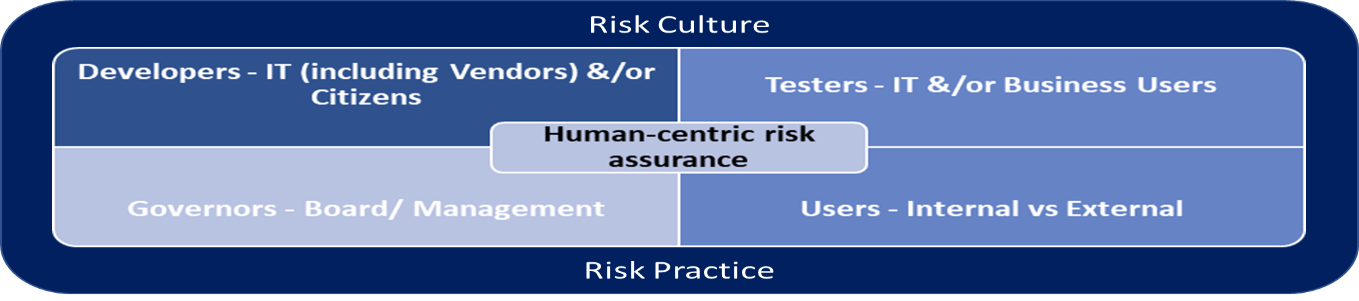
Regardless of which component, the underlying issue across all components is that everyone, other than risk & compliance professionals, does not acknowledge that they are not aware of or not receptive to risk management. These groups of people would assume that risk management is not their responsibility, these are the responsibilities of risk & compliance professionals. They have also stereotyped that risk management slows down their functional delivery. Hence, when each group of people carries out their responsibilities, only functional efficiency and effectiveness are considered. Risks have never been incorporated in their discussions and project designs.
Developers – IT (including Vendors) &/or Citizens: There has been a great promotion several years back about “Controls by Design” and “Security by Design”. These are approaches that developers can adopt to ensure vulnerabilities and risks can be mitigated prior to roll-out. It is too costly to perform damage control post implementation. Unfortunately, many developers were not given the opportunity for technology risks training. This becomes evident when auditors talk to the developers. To make matters worse, digital tools available allow organisations to push for citizens developers to encourage innovation and to control the developer’s talent crunch. The design and implementation risks of such digital tools roll-out heightened as citizens developers are not trained to design, develop and implement solutions properly. Audit has also discovered many issues relating to this matter and of the many issues I’ve observed, the key concern is that IT department was not aware of such developments in the various business units. IT department will not be able to govern when they are not aware of the existence of such projects.
Recommendation 1-2-3: (1) Establish a project governance process across all organizational business units and that all projects, regardless IT or Business Unit driven and zero cost or more, have to be registered with the Project Office prior any project procurement convenes. (2) Ensure mandatory targeted project training, including essential targeted ethics & security training, was received by the project design & development team members prior project commencement. (3) Establish a policy about information security that no approved freeware can be used for corporate projects.
Testers – IT &/or Business Users: Many testing audits noted poor test plans and test cases were used. The test plans and test cases were not complete, not co-designed by business users and testers were not properly trained to perform the tests. If the project is IT vendor led, most of the time vendors want to close the projects quickly and will push for test cases that may be “favorable” to their products to ensure a “pass”.
Recommendation 1-2-3: (1) Ensure the project plan has a proper testing phase that includes training the testers and test case design effort. (2) Ensure that the component of system testing versus functional testing versus user designed test cases versus vendor-provided test cases are not skewed e.g., 25% across and not 90% vendor-provided test cases. (3) Ensure that regardless of methodology applied, relevant training is provided, and documentation maintained i.e. scrum methodology versus conventional software development life cycle will have different expectations. Tweak the test approach accordingly and not “skip” it.
Users – Internal vs External: Data protection is key to users of any digital and technology solutions. The treatment of data and information should be classified and educated to all internal users. Internal users need to appreciate that corporate and personal information have to be managed with care and will face different consequences when leaked. The users involved in the leakage (and usually the negligence of the users) will have to be held accountable. Who can have access to the corporate and personal information have to be scoped out accordingly too.
Recommendation 1-2-3: (1) Establish a data usage and protection policy and ensure awareness provided to all internal users. Ensure vendors and external users have read your policy and acknowledge adherence and responsibilities accordingly. (2) Conduct crisis management simulation &/or training to internal users using data leakage scenarios and explicitly outline the sanction policy on such matters. (3) Verify your external users/ vendors control environmental strengths periodically.
Governors – Board/ Management: It is not enough to only talk about risks and whether they are controlled at reasonably acceptable level at risk committee meetings. Risk management has to be a strategy that goes hand-in-hand with all other business strategies. When risk management is incorporated in the DNA of an organization, it is no longer a perceived roadblock, it boosts outcome. There are many research conducted that agree that deploying risk management as a strategy will lead to positive business performance. Unfortunately, many Boards and Management Teams do not acknowledge that their risk management knowledge and risk responsibilities are lacking in some areas. The reality is that organisations that have risk and audit teams have much smaller teams as compared to business units’ staffing. This is logical understanding too. Hence, all the more for Boards and Management Teams to be pro-risk (beyond only financial risks focused) and incorporate risk management as a culture in all business dealings. In this way, risk and audit professionals can play their business partnering roles better and more effectively.
As outlined above, everything revolves around human resources. Training is key but many training are not effective as they are not right fit to the objectives that the trainees have been expecting or expected to have to fulfil their tasks. And many trainees do not appreciate the training received and hence never apply the relevant knowledge at work, leading to repeated audit issues noted. In addition, the recommendations listed above may seem easy to achieve but in reality, it is very challenging to execute them right.
Regardless of what your organization is deploying cloud, artificial intelligence or internet of things solutions, the above-mentioned are still valid. With technology, the impact of breaches can be fast and furious and can be escalated into crisis mode in a very short time. To stay resilient, your human resources have to be trained and prepared to act accordingly. Tools cannot make their own decisions. Hence, human-centric risk assurance maturity becomes critical.
And perhaps it is also the right time to make risk management a component of organizations’ balance scorecards. The scorecard should not be the number of audit issues considered as this drives negative auditees behaviour. I suggest perhaps consider the scorecard from a collaborative effort perspective e.g., number of risk-related training hours clocked, risk team invited to at least 20% of project discussion, audit team invited to perform readiness review of a key process, etc.
I will strongly recommend any organization in this digital era to (re) emphasize human-centric risk assurance effort, especially starting with hiring right and (re) starting the Code of Ethics awareness training programme. With encouraged employees’ creative way of working and work flexibility, sometimes, the gray area has widened, and this will cause organizational damages in many different ways. I am confident that should this concept and recommendations of mine be implemented right, fulfilling ESG & Sustainability mandates become natural and the incremental effort minimal.